Reclaiming Control: How to Achieve Full Energy Grid Asset Visibility Today
In the energy industry, your responsibility is clear: keep the grid stable, protect people from physical harm and service disruption, and stop adversaries from causing outages or damaging equipment.

TL;DR:
- Legacy CMDBs and agents were built for offices and data centers, not power grids. They routinely miss SCADA systems, PLCs, protective relays, RTUs, smart meters, and cloud assets that now carry real load.
- To achieve energy grid asset visibility, you need a live, agentless view across IT, OT, and cloud so teams can patch, segment, and respond with facts.
In the energy industry, your responsibility is clear: keep the grid stable, protect people from physical harm and service disruption, and stop adversaries from causing outages or damaging equipment. But IT/OT convergence is rapidly changing the ground beneath you. Every week brings new devices, new connections, and new blind spots. Without full energy grid asset visibility, you are managing risk with guesses instead of facts, and confident decisions turn into a gamble. Traditional IT tools weren’t built for today’s IT-OT environment and create a visibility blind spot that quickly becomes a real-world safety and reliability risk.
The challenge of securing the modern energy sector is enormous. For CISOs, Security Directors, and OT/ICS Security Engineers in the Energy and Critical Infrastructure Sectors, the work now spans IT, cloud, and Operational Technology (OT). The critical foundation of complete and accurate asset visibility is often missing. When it is missing, disciplined risk management becomes a complex bet.
Why Current Security Tools Can No Longer See the Network
There is a mismatch between what converged networks need and what legacy tools provide. Converged systems require real-time, safety-aware context. Legacy tools were designed for yesterday’s static IT environments. The gap is widening on two fronts: an increase in unmanaged devices and a rise in faster, more numerous threats.
The Double Attack Surface: IoT Influx and High-Velocity Threats
Industry signal: KPMG on the IoT influx
The influx of new, unmanaged devices is radically changing the perimeter. KPMG notes that security is being reshaped by the influx of smart and IoT devices deployed across generation, transmission, and distribution assets. Every new environmental sensor, smart meter, or remote substation device becomes a network endpoint and entry point that sits outside yesterday’s security model. This accelerating growth introduces many non-standard, low-powered assets that conventional methods cannot manage safely or consistently, which expands the places an attacker can land and move.
Threat tempo: IBM X-Force findings
The urgency is compounded by the speed of threats. IBM X-Force reported 670 vulnerabilities that could impact OT in the first half of 2025, with 49% rated Critical or High and public exploit code available for 21% of the Critical flaws. You cannot mitigate hundreds of high-severity issues in six months without complete energy grid asset visibility. If you miss even five percent of assets, dozens of critical systems can remain unpatched while adversaries move faster than traditional patch cycles.
The Failures of Static Inventory and Intrusive Agents
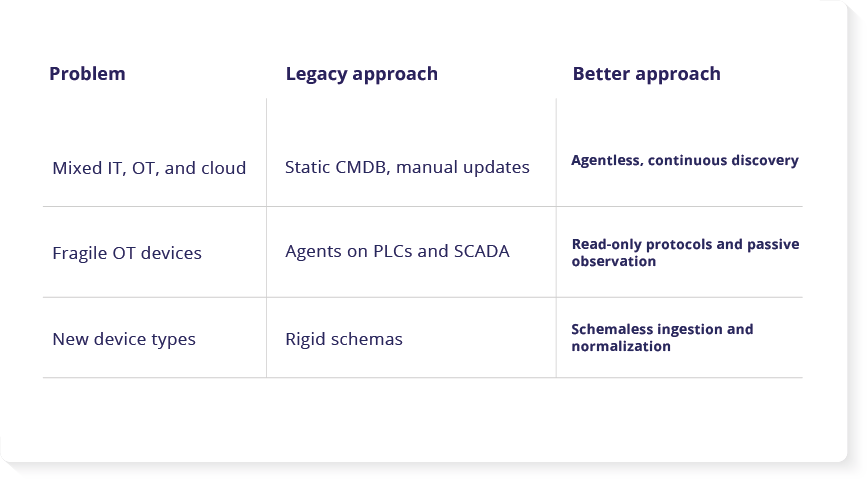
The CMDB and spreadsheet trap. Static CMDBs and spreadsheets impose rigid schemas designed for known IT environments. Bespoke OT assets and ephemeral cloud resources do not fit, and manual updates only capture the last known state. That leaves a dangerous gap between documentation and reality.
The agent barrier. Traditional agents are a non-starter on sensitive PLCs and SCADA. They can void warranties, add latency, and destabilize fragile processes. Many low-power devices cannot run an agent at all. Read-only methods are safer for devices like protective relays and RTUs that maintain critical functions.
What we mean by “Energy Grid Asset Visibility”
Energy grid asset visibility is a continuously updated, agentless view of every asset and dependency across IT, OT, and cloud, including identity and ownership, location, software and firmware, network paths, and policy status, so patching, segmentation, and incident response are based on facts, not guesses.
The New Blueprint: Non-Negotiable Requirements for True Energy Grid Asset Visibility
Security leaders can move from a static list to a living knowledge model, a dynamic source of truth that supports decisions across IT, OT, and cloud. That shift needs three things:
- Agentless, read-only discovery is mandatory.
Use passive traffic observation, APIs, and read-only methods that are safe for OT and ICS. No agents on fragile devices. No impact on operations. Align this approach with frameworks like IEC 62443 and map detections to MITRE ATT&CK for ICS for shared understanding. - Real-time and dynamic data collection.
The estate changes by the minute as cloud resources spin up and down and endpoints connect and disconnect. Inventory must update continuously so patching and response decisions match reality. - Schemaless flexibility for all asset types.
Convergence introduces a multitude of device types and data shapes. A schemaless architecture ingests data from various sources, including network scanners, cloud APIs, and OT protocols, and normalizes it without brittle templates. This keeps energy grid asset visibility comprehensive as the environment evolves and supports programs that reference NERC CIP standards without making compliance claims.
How WanAware AIM Delivers Energy Grid Asset Visibility
WanAware Asset Inventory Management (AIM) is built for energy grid asset visibility across IT, OT, and cloud. It meets the three requirements:
- Agentless, read-only discovery. Uses passive observation, safe OT protocols, and APIs to inventory assets without agents on PLCs, SCADA, protective relays, or RTUs.
- Real-time and dynamic updates. Continuously refreshes asset state so patching, segmentation, and incident response reflect what is actually connected, including substations and cloud resources.
- Schemaless flexibility. Ingests and normalizes any device or data source, including OT protocols and cloud APIs, so new asset types do not break the model.
With AIM, teams stop guessing and start confirming. You see what each asset is, where it lives, who owns it, what it talks to, and whether it is safe and current. That live context strengthens energy grid asset visibility and supports work aligned to IEC 62443, NERC CIP, and MITRE ATT&CK for ICS.
To see how the same platform helps telecom teams reduce OpEx, you can read our telecom asset discovery article.

Next actions checklist
- Inventory with agentless, read-only discovery in production OT
- Update continuously to capture ephemeral cloud assets and dynamic endpoints
- Normalize any device data with a schemaless model
- Tie assets to ownership, location, software and firmware, network path, and policy status
- Run patching and segmentation from the living inventory, not spreadsheets
How to get started with WanAware AIM
- Scope the first zone. Choose a substation segment or plant network to baseline what is connected.
- Run a safe, read-only discovery. Use AIM to passively inventory assets and dependencies across IT, OT, and cloud.
- Validate ownership and paths. Confirm owner, location, software and firmware, and network paths for each asset.
- Act on the findings. Fix stale entries, close orphaned trusts, and target patching and segmentation from the live inventory.

Frequently asked questions
What is energy grid asset visibility?
A live, agentless inventory of every asset and dependency across IT, OT, and cloud with ownership, location, software and firmware, and network paths updated continuously.
Why are agents risky in OT?
Agents can affect latency, void warranties, or destabilize sensitive PLC and SCADA systems, and many low-power devices cannot run agents.
How does visibility improve patching and segmentation?
Real-time context ensures patches target the right assets and segmentation reflects current dependencies so changes do not break critical processes.
Your next step to confident security
The risk facing the energy sector is real, and it can be managed with the right foundation. You cannot secure what you cannot see, but you can achieve full, confident visibility. Move beyond manual, static tools that no longer fit today’s converged network. See how WanAware AIM delivers complete visibility across your IT, OT, and cloud estates, bringing previously unknown assets into focus and strengthening energy grid asset visibility across the board.