Telecom Asset Discovery: Unlock Real OpEx Savings
Most telcos see sub‑1% OpEx gains from AI today. Telecom asset discovery keeps inventory current with always‑on, agentless collection and clean outputs, so automation can unlock real savings.

Executive Summary
• Despite $300B+ invested since 2018, and CapEx being flat or up for 85% of telecom operators, ROIC has fallen 10–15%. The gap is asset visibility: leaders can’t manage what they can’t see.
• AI is touted for double‑digit OpEx reductions, but most telecom operators report sub‑1% realized so far. Root cause: Incomplete, stale, siloed inventory that cannot keep up with CNFs, edge, and fast change.
• Critical first step: Real-time asset discovery with WanAware AIM: always‑on, agentless, and non‑intrusive; no installs, no credentials; continuously detects changes and leverages existing tools and logs.
• Immediate wins: Eliminate ghost assets, reconcile licenses, cut energy, shrink MTTI, and finally feed AI clean, trustworthy data.
Source: 2025 WanAware Telecom Observability Benchmark (n=180, North America & Europe).
Telecom Asset Discovery: The fastest OpEx gains start with a clean, current asset list
Telecom networks are quietly turning into cost machines that outpace every budget cut. It's challenging to reduce operating costs when yesterday's network and obligations are hindering progress. Despite investments, energy bills, license renewals, truck rolls, and SLA credits continue to creep up. Meanwhile, 5G rollouts, fiber, VNFs and CNFs, and edge sites are multiplying the moving parts. The potential for savings is great, but early AI and automation pilots are delivering sub‑1%. The issue is not the algorithms. It is the inputs.
Why telecom asset discovery is the first step to savings
During outages and change windows, teams still struggle to answer two basic questions. Which functions are running where? Which changes will break them next?
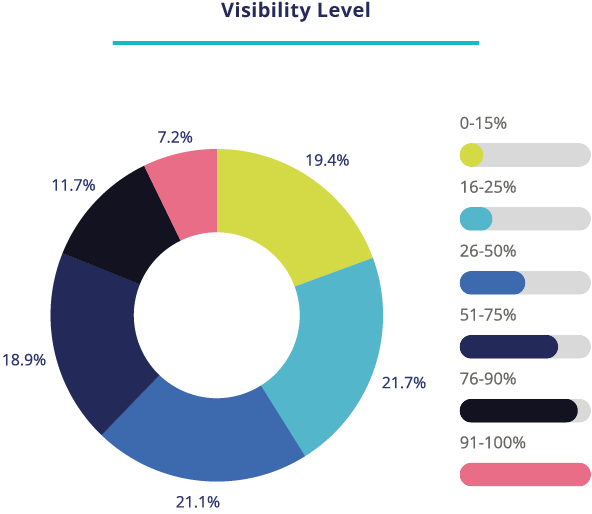
Today only 7% of leaders report near-complete visibility, while 62% can see less than half of their assets. You can’t automate what you can’t see. (2025 Benchmark)
• Old and new gear mixed together: 2G and 3G and copper live alongside fiber, 5G core, and cloud.
• Functions running in different ways: VNFs on virtual machines and CNFs on Kubernetes that scale up and down.
• Many small sites changing constantly: Edge locations and micro sites that add, move, or retire assets frequently.
The result is a growing visibility debt that blocks safe power-downs, right-sizing, and decommissions.
When the asset record is incomplete or out of date, operations cannot safely power down, right‑size, or decommission. AI ends up guessing, so leaders see sub‑1% impact instead of the gains they expected.
Most teams see less than half of their assets today

How Inventory Is Managed Today (and Where It Breaks)
Most operators run a careful process that made sense when networks changed slowly. This section explains how inventory is maintained today, why that approach struggles with cloud and CNF pace, and what a modern, low‑friction path looks like. Read it as a reality check and a practical checklist you can reuse in your next review meeting.
Current approach
Most teams combine a few dependable methods: CMDB updates tied to change tickets and quarterly audits; vendor OSS and element managers for each domain; periodic scans or SNMP and CLI scripts; spreadsheets for license and contract true‑ups; and manual reconciliation across naming schemes and owners.
We go deeper on common CMDB problems and options in our CMDB article.
Where it breaks
These methods work, but they lag the way assets behave now. Fast-moving CNFs, short-lived workloads, and lab gear promoted to production often slip past quarterly cycles. Each domain keeps its own picture, so RAN, transport, core, data center, cloud, and edge do not stay in sync. Peering links, virtual interfaces, and cloud accounts without a clear owner create blind spots. Model names, serials, and locations drift across systems. Most importantly, there is no clear signal of confidence that tells you whether a fact is verified, inferred, or stale.
Budget priorities reinforce the problem: 54% allocate ≤10% of infra budgets to observability (and 32% spend just 0–5%). Tool sprawl adds friction—30% of teams juggle 7+ tools. (2025 Benchmark)
What needs to change
To maintain a current inventory, you need a tool that matches how assets behave today (elastic, ephemeral, multi‑cloud) rather than how networks looked when many inventories were built (static, on‑prem, ticket‑driven). In practice, that means:
• Always‑on discovery that listens to control planes and logs instead of waiting for quarterly audits
• Agentless, non‑intrusive collection (no installs, no credentials) safe for sensitive gear and brownfield
• Real‑time change detection so CNFs that scale or move are reflected within minutes, not months
• Normalization and de‑duplication across vendors and domains to one schema people can actually use
• Field‑level confidence and lineage so teams know which facts are verified, inferred, or stale
• Operational attributes (owner, site, lifecycle, version, last‑seen, power class) so decisions are actionable on day one
• Open outputs so performance, availability, and security act from the same record
If you are also moving more workloads to cloud, this cloud journey article explains why migration is an ongoing process.
What changes with WanAware AIM (Asset Inventory Management) for telecom asset discovery
Before you can take advantage of any automation and its potential for savings, the first step is to know what assets you have in real-time. Start with a single, continuously updated inventory of assets.
AIM Asset Discovery delivers:
• Always‑on, agentless, non‑intrusive: no installs, no credentials; leverages existing tools and logs
• Continuous freshness: detects changes in real time so CNF scale‑outs, moves, and retirements are reflected quickly
• Normalized attributes: vendor, model, role, owner, site, lifecycle, version, last‑seen, power class (where available)
• Confidence and lineage: show what was learned, when, and from which source
Put simply, you get one current truth that is accurate enough to act on.
Why one record matters for Performance, Availability, and Security
A single, trustworthy inventory becomes shared input across teams:
• Performance: right‑size capacity and power budgets using accurate counts and versions
• Availability: faster MTTI with current owner/site/role so incidents route correctly
• Security: reduce attack surface by finding unknown and EoL/EoS devices and unapproved images
Immediate wins from telecom asset discovery you can measure this quarter
With 80% of teams saying monitoring is still mostly manual, the fastest wins come from a current, trustworthy inventory. And without better inputs, 32% report no downtime reduction from AI tools (2025 Benchmark). Stale inputs = stale outcomes.
• Shrink MTTI: know where assets live and who owns them so you can prove domain faster
• Eliminate ghost assets: stop paying power and licenses for equipment you thought was retired
• Decommission safely: verify ownership, role, and lifecycle state before you turn anything off. Reduce risk and cost
• Contract hygiene: reconcile actual counts to licensed counts and avoid overage fees
• Energy targeting: find idle chassis and forgotten line cards for power‑down windows
• Feed AI cleanly: trigger models on verified assets and attributes, not spreadsheets
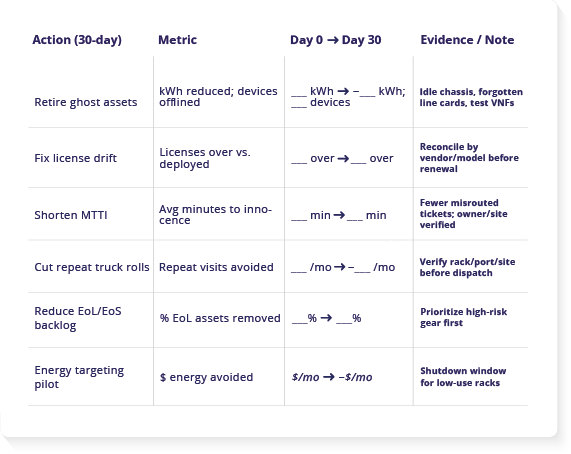
First-30-Day Wins Scorecard
Telecom asset discovery in practice (fast pass)
Here is a quick look at what a modern inventory captures in each telecom domain. Think of it as what gets listed, how it’s labeled, and why it’s useful on day one. We are not modeling service paths here; we are collecting the facts: what exists, where it resides, who owns it, its current state, and when it was last observed, so operations can act with confidence.
As footprints expand, 25% aren’t confident in visibility for new or expanded sites, and nearly 40% say >25% of the network is insufficiently monitored—another reason the inventory must stay live. (2025 Benchmark)
RAN
Discover radios and fronthaul gear, confirm site and sector inventory, and associate owners and tenants.
Transport
Catalog L2 and L3 devices, ports, VRFs, label stacks. Tie assets to sites and roles for planning and retirement windows.
Core
Inventory 5G SBA functions like AMF, SMF, and UPF plus VNFs and CNFs, with current placements and lifecycle states.
Data center and edge
Tie compute and storage assets to sites. See what is safe to right‑size or shut down with owner and lifecycle checks.
First action to take: use this list to flag idle chassis, forgotten line cards, and test VNFs for the next change window.
Outcome
The first confident list you can operate from, because it updates as the network changes.
WanAware AIM: Your guide to telecom asset discovery’s first step
You set priorities and own changes. The list below explains how AIM keeps your inventory fresh and trustworthy—so when you act, you’re acting on facts. Pair these platform capabilities with the decision signals in the next checklist to choose what’s safe to touch now and what should wait.
• Always‑on, agentless, non‑intrusive: no installs, no credentials; safe for sensitive gear
• Continuously updated record: physical, virtual, cloud assets with owner, site, lifecycle, version, last‑seen
• Normalization and de‑duplication: one schema with confidence and change lineage
• Leverages existing tools and logs: widen coverage without new agents
• Low friction, fast value: reach a trustworthy baseline inventory and shorten time to impact
How AIM indicates “safe to touch” (within inventory scope)
AIM does not automate changes; it surfaces operational signals that lower risk when you choose to act. Typical “safe‑to‑touch” candidates are assets where:
• Lifecycle = test, lab, or decommission‑pending, not production
• Last‑seen shows no traffic/heartbeats for a defined window
• Owner and site are verified, so the right teams can approve quickly
• Version/EoL status suggests replacement is due and maintenance is scheduled
• Power class / utilization hints suggest idle capacity
• Confidence + lineage confirm facts are fresh and source‑backed
Use these signals in conjunction with your change process to plan energy shutdowns, license true-ups, or decommissioning. For anything ambiguous, AIM helps you route to the right owner fast.
With AIM, your team gains the operational certainty to eliminate ghost costs now and feed AI the data it needs to deliver more than sub‑1%.
Benchmark your network against 180 telecom operators
Only 7% report near-complete visibility, and most see less than half of their assets. Want to know if you’re ahead of the pack or falling behind? The 2025 Telecom Observability Benchmark shows how your peers budget for visibility, where blind spots are most painful, and which moves correlate with better ROIC and OpEx savings.

FAQs
What is the difference between a VNF and a CNF?
A VNF is a network function packaged as a VM. A CNF is a cloud‑native microservice in containers orchestrated by Kubernetes. CNFs scale and move quickly, which breaks static inventory unless updates are continuous.
Why does inventory determine OpEx savings?
Automation is only as safe as its inputs. If you cannot trust the asset list and attributes, you cannot power down, consolidate, or decommission with confidence. Savings stay small.
Is agentless discovery safe for sensitive equipment?
Yes. API and telemetry approaches avoid installing agents on sensitive gear and avoid aggressive active scans, while still building a verified record.
Can AIM help with data sovereignty?
Yes. AIM shows where assets and workloads are recorded to run so you can prove regional boundaries for compliance and premium offerings.