When a Critical Vulnerability Hits Your Grid: OT Asset Inventory for Faster Response
When a critical vulnerability hits your grid, your phone lights up almost immediately.

Security wants to know the impact.
Operations wants a list.
Leadership wants to know one thing: “Are we exposed, and where?”
You know field crews cannot touch a single device until you answer that question with confidence.
But the moment you look at your “inventory,” reality hits.
- The CMDB is partial and months out of date
- Firmware fields are blank or missing
- Substation locations are wrong or not filled in
Spreadsheets disagree with what is actually in the field
You are on the hook to give a clear answer. But you are staring at data you do not really trust.
All of this is happening while you’re under time pressure, you only have short, approved time windows to take systems offline, and you know an auditor will eventually ask how you figured out which assets were affected.

Why OT Asset Inventory Often Fails When OT Security Needs It Most
In a calm week, outdated inventory is annoying. During a critical vulnerability, it becomes a real risk.
Industry guidance is clear on this. According to CISA’s Foundations for OT Cybersecurity: Asset Inventory Guidance, asset inventory is the first building block of a defensible OT architecture. Yet most energy organizations still struggle to maintain an accurate, up-to-date list.
NIST’s Cybersecurity Framework reinforces the same idea. It puts asset management at the center of the Identify function because every other control depends on knowing what you have and where it lives.
If you want to see how that plays out in real energy environments, our guide on achieving full energy grid asset visibility today walks through what full grid visibility looks like in practice.
In practice, we see the same three failure patterns again and again.
1. Static data in a real-time problem
Most OT asset inventory tools were not built for how fast your grid changes now. New devices go live, configurations get tweaked in the field, and temporary setups turn into “just how it is” long before anyone updates a system.
- New devices come online between audits
- Temporary configurations become permanent
- Changes happen in the field that never make it back to the CMDB
We break down why traditional CMDB tools keep failing in more detail in our blog on why your CMDB tool never fails to fail you.
So when a high-risk security advisory comes in, you are querying data that no longer reflects the current reality. You either miss exposed assets or spend days checking equipment that is not actually affected.
2. No place to put what you now need
OT vulnerabilities often come down to very specific details:
- Exact firmware versions (for example, RTUs stuck on 4.2.7 instead of 4.3.1)
- Particular library builds (a specific crypto or communications library version that is now vulnerable)
- Vendor patch levels (which relays have had the latest security update installed, and which have not)
The moment you try to search by those details, you discover the system has no place to store them. Or adding new fields requires a change request, a project, or a vendor ticket. You finally know what you need to search for, and your system has nowhere to put it.
3. The “where” and “who” questions are still unanswered
Even if you know which models and versions are affected, you still need to know:
- Where is each device? (Substation 4B, Pump Station North, Control Room A)
- Who owns it? (Which regional operator or crew is responsible?)
Most inventories stop at a logical asset ID. They do not tie it cleanly to a physical place and an accountable owner.
Missing information like this does more than slow you down. It strains relationships. Security looks pushy for asking for “one more list.” Operations feels blindsided by late urgent requests. Compliance sees the risk building while everyone argues over whose spreadsheet is right.
WanAware AIM OT Asset Inventory: One Place You Actually Trust in a Crisis
When a vulnerability shows up, you do not need another dashboard. You need one place you trust to answer:
“Which exact devices match this advisory, and where are they?”
That is what WanAware AIM’s OT Asset Inventory is built for. It gives energy and utilities teams a live, accurate view of OT assets, ready before the next advisory shows up.
For a broader look at how OT asset inventory fits into grid-wide resilience, download our whitepaper on how WanAware supports energy and utilities teams.
1. Always-current OT inventory, without agents or scans
AIM continuously ingests data from your existing logs, systems, and sources. There are no agents to deploy, no intrusive scans to schedule.
So when you open WanAware during a critical vulnerability, you are not spinning up a project.
You are looking at a current view of:
- SCADA servers
- RTUs and PLCs
- Protection relays and field devices
- Supporting infrastructure across IT and OT
Your team goes from “we think this is the latest spreadsheet” to “this is the source of truth we can act on.”
Instead of a static CMDB, you have a real-time OT asset inventory that keeps up with daily change.
2. Flexible enough for the details a critical vulnerability depends on
Because WanAware Asset Inventory is schema-less behind the scenes, you are not stuck waiting for new templates whenever a new kind of data shows up.
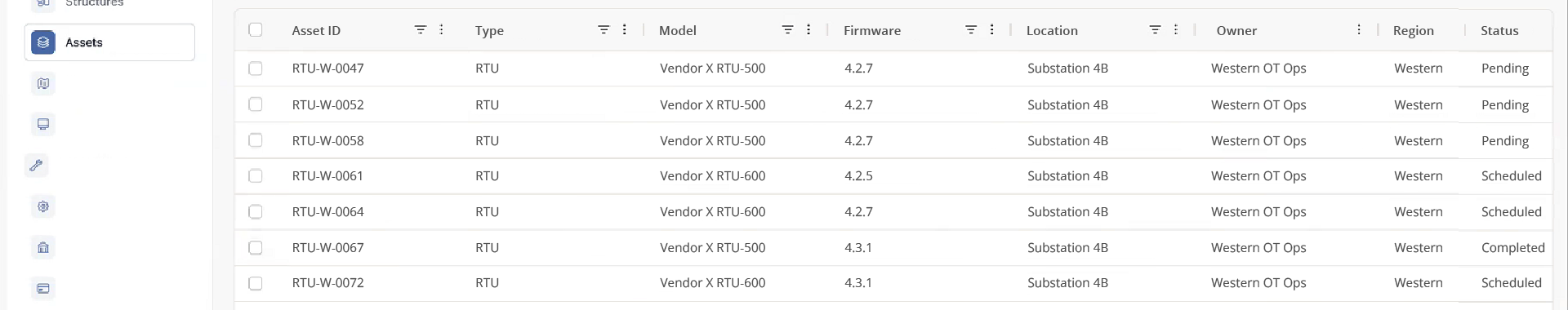
If an advisory depends on firmware version 4.2.7, a specific build or library, or a vendor patch level, you can capture that detail in the inventory and search on it right away. No redesign of the CMDB. No rework of a data model.
Your analysts can run precise searches like:
“Show all RTUs with firmware 4.2.7 in the Western region.”
Instead of guessing or over-including, you isolate just the devices that matter.
3. Every asset tied to location and ownership
Each asset record in AIM can be enriched with:
- Physical location (substation, station, site)
- Region or line of service
- Responsible owner or team
So when you hand results to operations, it is not just a list of IDs. It is a set of clear work items:
- “These ten devices in Substation 4B, owned by this regional crew.”
- “These specific relays at Pump Station North, owned by this team.”
The missing information that used to spark back-and-forth emails disappears. Everyone sees the same list and knows what they are responsible for.
From Days to Minutes: What Changes When You Can Trust OT Asset Inventory
In many organizations, a serious OT advisory still triggers a familiar pattern:
- Security sends out the initial alert
- OT scrambles to pull exports from the CMDB and vendor portals
- Regional ops teams send spreadsheet fragments and screenshots
- People argue about which list is “most accurate”
- Maintenance windows slip while everyone tries to line things up
By the time there is enough confidence to send a crew, days have gone by, and the risk has been sitting in the environment the whole time.
With WanAware’s asset inventory capabilities in place, the sequence starts differently:
- You open a real-time inventory that is already in sync with your environment
- You add the specific fields the advisory cares about, if they are not there yet
- You run a focused search and immediately see which assets match, where they are, and who owns them
The long, manual verification phase goes away. You open AIM, run a focused search, and get the list you need in seconds. That gives you a chance to use the outage windows you already have, instead of waiting for the next one and carrying more risk.
It also changes the tone of every conversation:
- Leadership hears: “Here is the list, this is how we built it, this is who is working it.”
- Auditors hear: “Here is the system of record we used, and the query we ran.”
- Operations hears: “Here are your assets, here is the location, here is what we need you to do.”
You move from “we are doing our best with what we have” to “we know exactly which assets are in scope and we can prove it.”
Build Future Resilience on a Foundation You Can Explain
Every future improvement you want, from better monitoring to deeper analysis, depends on one thing: an inventory you can explain and defend.
WanAware AIM does not try to do everything at once. It gives you:
- A single, real-time source of truth for OT assets
- The flexibility to capture new vulnerability details as they appear
- Clear ties between assets, locations, and accountable owners
That becomes the base layer for tighter incident response, better change planning, and stronger audit readiness. None of it works if you do not trust the list of assets you are protecting.
Learn more: WanAware Asset Inventory
If you also oversee IT environments, read Why IT Asset Visibility Is Your Company’s Strategic Edge to see how the same principles apply beyond OT.

FAQs: OT Asset Inventory and Critical Vulnerability Response for Energy Companies
What is OT asset inventory in the energy sector?
OT asset inventory in the energy sector is a real-time list of all operational technology assets that keep the grid running. It includes devices like SCADA servers, RTUs, PLCs, relays, and other field equipment, along with their firmware, location, and owner. A strong OT asset inventory helps you see what you are defending and how to act when a new vulnerability appears.
Why is real-time OT asset inventory important during critical vulnerabilities?
Real-time OT asset inventory is important during critical vulnerabilities because it lets you quickly answer, “Which devices match this advisory, and where are they?” If your inventory is static or out of date, you either miss exposed assets or waste days checking the wrong devices. A current view of your OT environment lets you move from awareness to action within your existing maintenance windows.
How does OT asset inventory support NERC CIP and audit readiness?
An accurate OT asset inventory supports NERC CIP and audits by providing a clear system of record for which assets exist, where they sit, and how you identified them during an event. When auditors ask how you scoped an advisory, you can show the inventory you used and the search you ran, instead of pointing to conflicting spreadsheets. For more on these requirements, see NERC’s official Critical Infrastructure Protection (CIP) Reliability Standards.
How is OT asset inventory different from a traditional CMDB?
A traditional CMDB is usually built for IT assets and can be slow to change. OT asset inventory focuses on the devices and systems that control the grid and updates as the environment changes. It can store OT-specific details like firmware versions and substation locations, which are essential for OT vulnerability management and critical vulnerability response.
Do I need OT observability to benefit from WanAware AIM?
No. WanAware Asset Inventory Management (AIM) delivers value on its own by giving you accurate, real-time OT asset inventory. You can identify and locate vulnerable devices faster, support NERC CIP and audit needs, and reduce the back-and-forth between security, OT, and field operations. WanAware’s Actionable Observability module is an upgrade on top of this foundation. Once you trust the inventory, observability builds on it by showing asset behavior, spotting early signs of trouble, and mapping dependencies so you can see potential impact before something breaks. Explore how observability works in WanAware.