Cybersecurity Actionable Observability
See every connection, understand every risk, and protect your entire enterprise in real-time
Get the power to see, understand, and protect your environment in real-time. By moving beyond static inventory lists to a Relationship Graph, you gain the clarity needed to ensure operational resilience, secure your most critical assets, and drive business value with mathematical certainty.
Start Free Trial
30 Days (No credit card required)
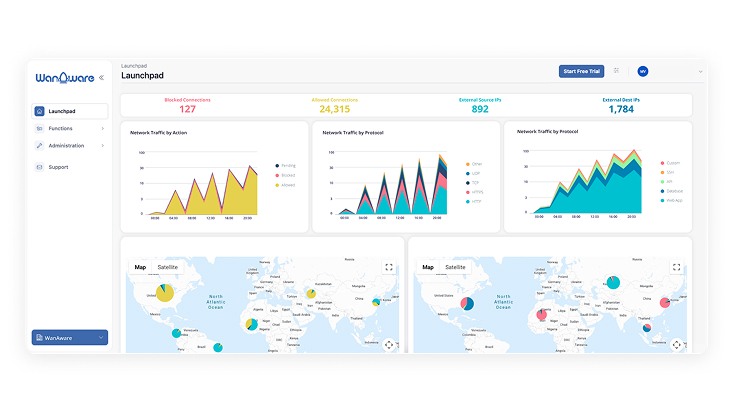
The Power of Integration: EASM, Vulnerability Scanning, and the Relationship Graph
By unifying External Attack Surface Management (EASM) and Vulnerability Scanning within the Relationship Graph, you move from reactive monitoring to strategic command. This integrated approach provides a holistic view that ensures your security posture is always aligned with your operational reality.
See how this works in your own environment.
Start Free Trial
30 Days (No credit card required)
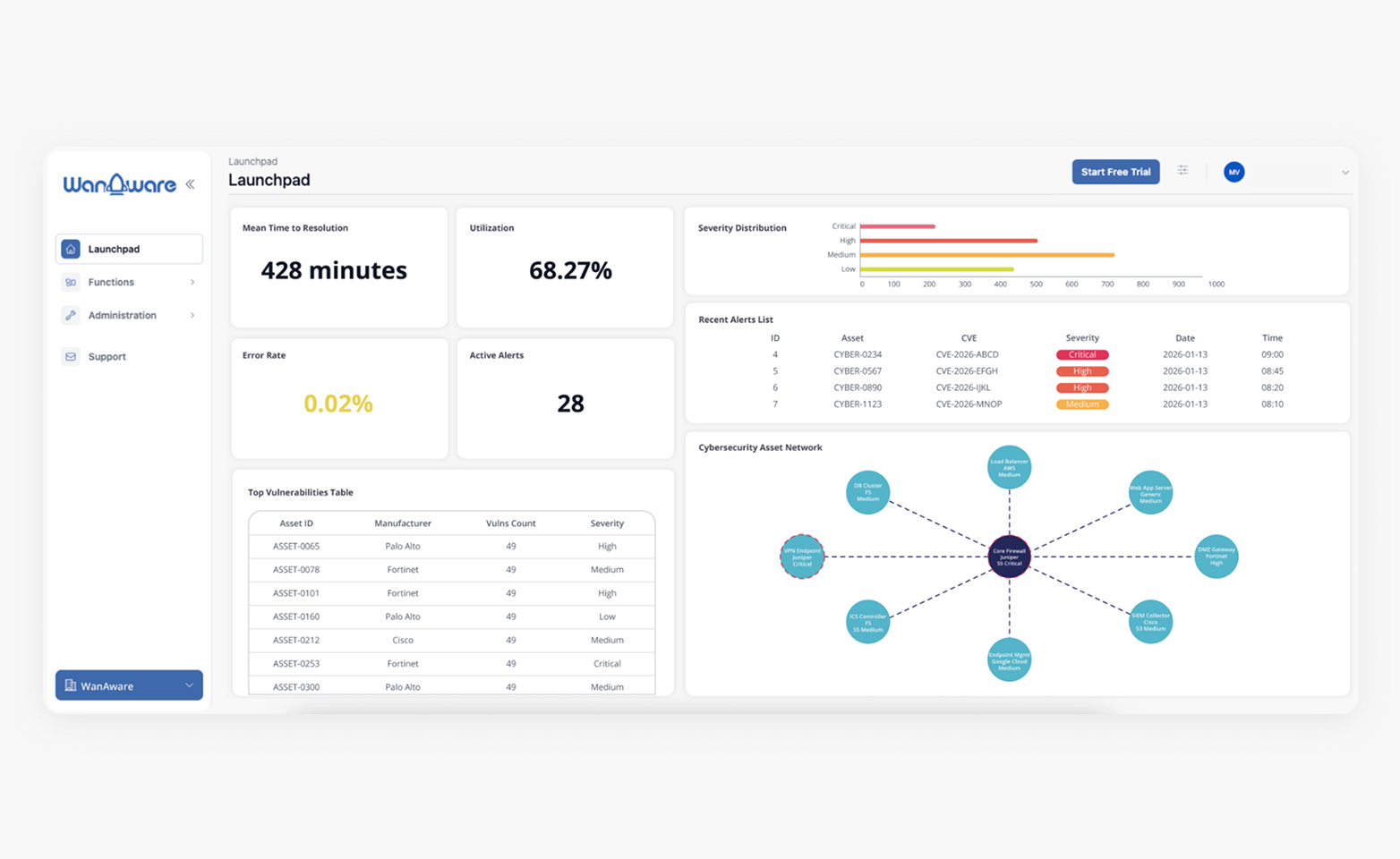
Accelerate Resolution with Precise Intelligence
- Instant Root Cause Identification — Experience a 90% reduction in Mean Time to Resolution (MTTR) by identifying the exact origin of incidents through deterministic causal inference.
- Intelligent Noise Suppression — Filter out up to 90% of operational noise automatically, ensuring your team engages only with high-fidelity, actionable alerts.
- Proactive Guidance — Receive automated, pre-digested reports that detail the root cause and the specific next steps required for resolution.
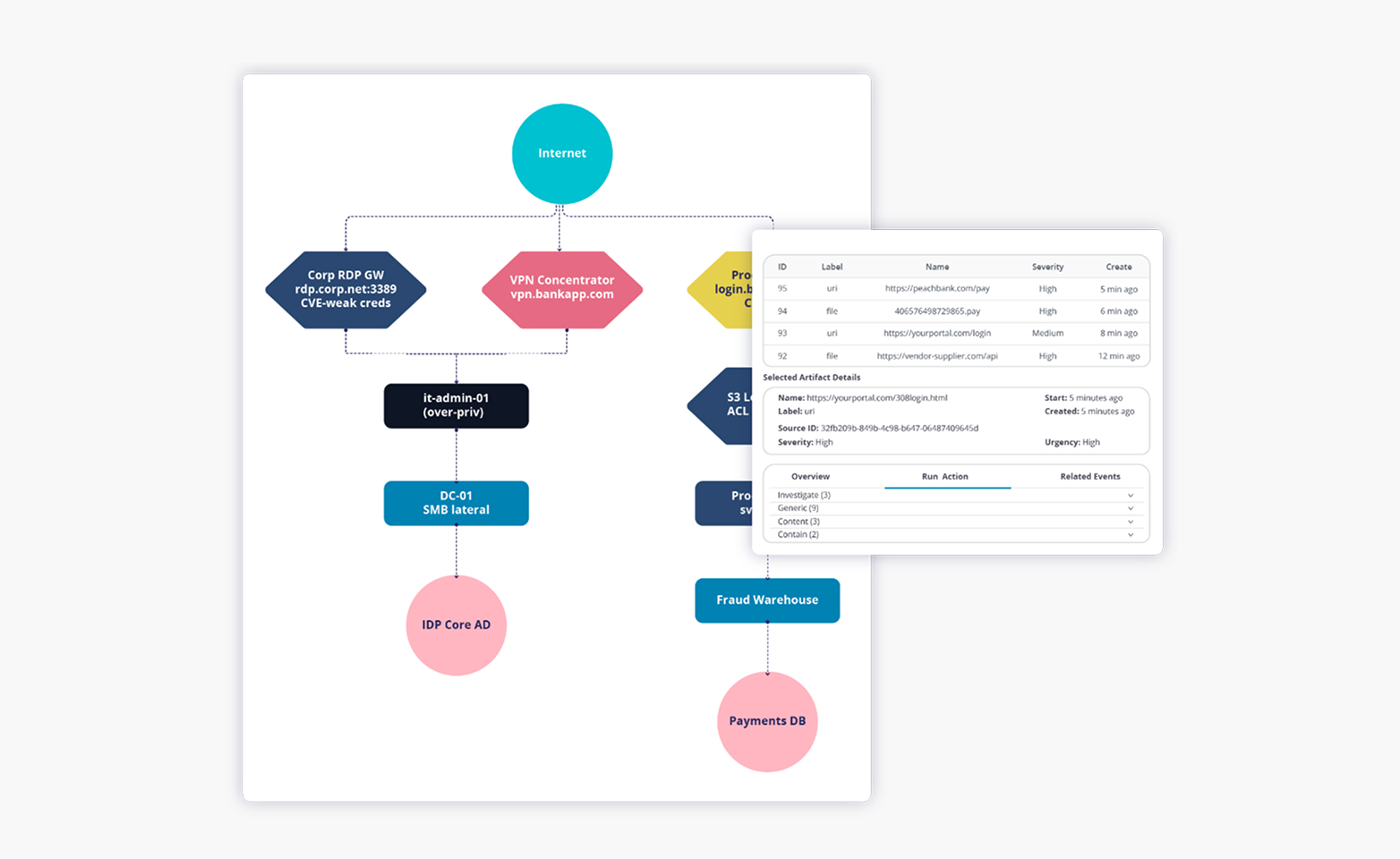
Prioritize Risk with Contextual Intelligence
- Strategic Risk Focus — Focus your remediation efforts on vulnerabilities that are actually reachable from the public internet, ensuring you protect what matters most.
- Visualize Lateral Movement — Instantly see potential attack paths an adversary could take through your infrastructure and network to reach your "Crown Jewel" assets.
- Verified Zero Trust — Enforce security policies based on the verified, observed reality of your network topology, moving beyond assumed policy to absolute certainty.
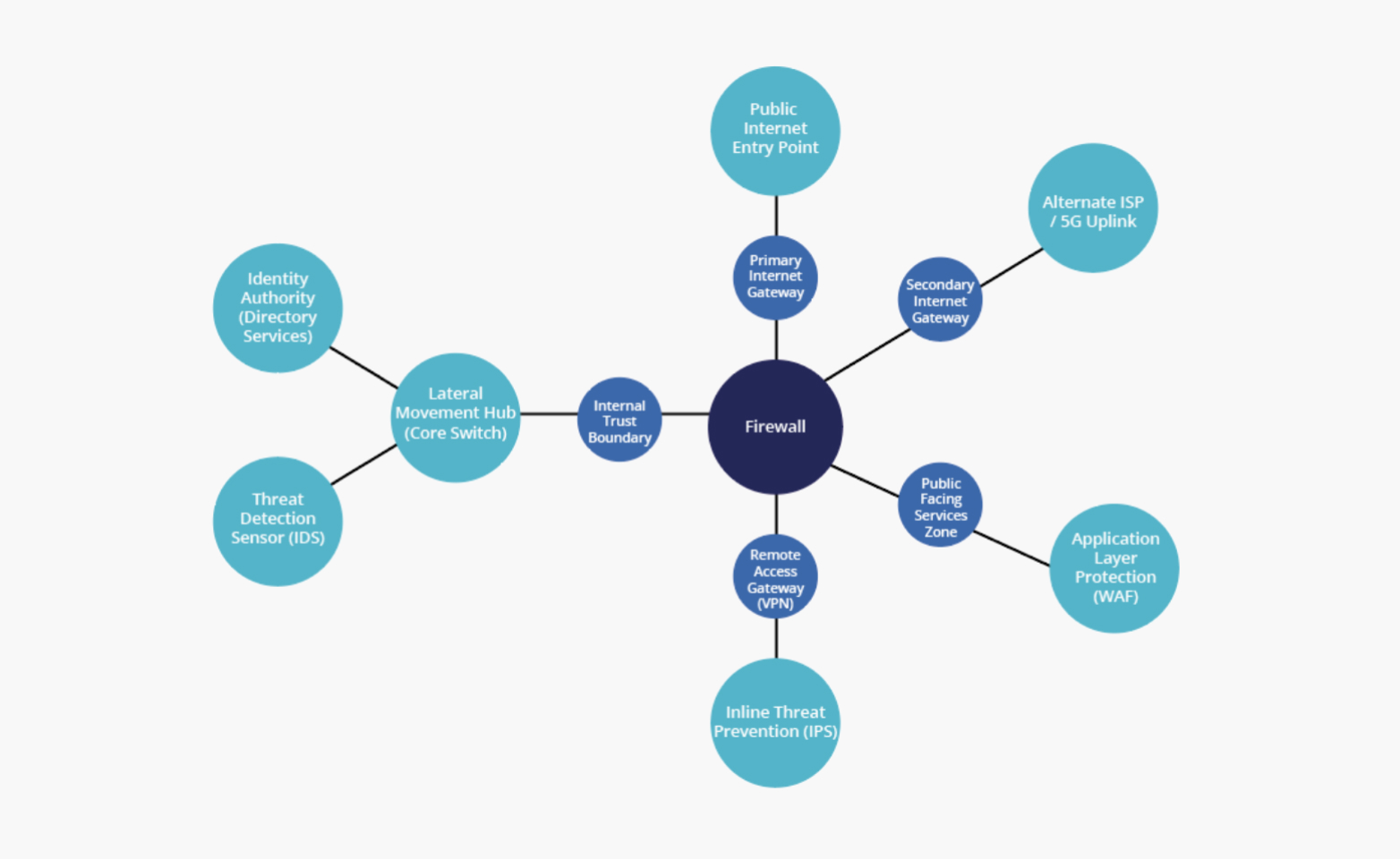
Master Your Global Visibility
- Uncover Every Asset — Leverage over 160,000 ephemeral agents to discover internet-facing IPs, domains, and services that traditional tools miss.
- Adaptive Discovery — Maintain a live, schema-less record of everything from cloud-native microservices and IoT to industrial OT and medical devices.
- Third-Party Resilience — Monitor upstream dependencies like SaaS providers, CDNs, and ISPs with the same rigor as your internal systems to stay ahead of external outages.

Maximize Economic and Regulatory Value
- Strategic Cost Savings — Confidently decommission "Zombie Servers" and unmanaged resources by verifying they have no active business dependencies, reducing cloud spend by 20-30%.
- Automated Compliance — Generate real-time documentation for HIPAA, NERC CIP, and Reg SCI audits in seconds, replacing weeks of manual evidence collection.
- Predictive Impact Analysis — Use "Digital Twin" simulations to see the predicted impact of changes before they are deployed, preventing self-inflicted outages and preserving revenue.



